What to do if one of these "congratulations, you have been chosen"emails has found its way into the Inbox? Most people press with a shrug, the delete button and consider it done. But not all of them. The magazine Heise.de has published a report this week in which an experienced Hacker describes anonymous in his counter, after he had been informed in a mail message that he had inherited 10 million dollars.
First of all, the Hacker visits the site that it the scammers to entice you. He is there to make a payment of 2500 dollars, to the payment of the million can amount to be taken: typically for advance fraud. Since this site is poorly protected, can penetrate the hack in the database on the dispatch of the Spam messages will be handled. In the administration area, he deposited a Script, and attracts the scammers under a pretext. When you Login, the Script registers the IP address of the fraudster operates. This IP address leads the hackers to the Internet connection and the Router of the swindler.
The default password
Because the Router the default password was never changed, changed, the Hacker can log in and make adjustments. In this way, he monitored the activities of the swindler. This is more the employment of the dispatch of spam mails. The Hacker now has the login details for the ADSL access. Since the IP address of the Internet provider, tried the hack, whether the access data work in the customer portal of the Provider. And, in fact: With these data, he logs on and gets to the name of the swindler. Finally, he determined its location.
of Course – the fine Art it is not: a vigilante is also in the digital space is not a trivial offence. Who breaks into other Computer, commits an offence, whether he is now chasing criminals or not.
But you don't need to be for the hackers to retaliate. An opportunity for a legal return carriages, with fake support calls. In this Scam, which is practiced since soon ten years, reports by telephone to a Person claiming to be a Supporter of a big Tech company like Microsoft, and claims that it is a computer problem, for example, a virus infection or a "constipation" with temporary files. The actual intention is to steal personal data or to sell expensive, useless security programs.
User strike back
Now some people make the Fun to make fun of the callers themselves: you wonder term, repeat every word of the caller, or to catch, to hold long monologues about God. There are also people, the "Moment" to say and the listener, aside and have the caller wait until he hangs up. Some place it is also important to take the scammers for their part in the defect, and to elicit from them information – or even the confession that everything is just misleading.
But there are also cautionary voices: to fall The fraudsters on the nerves, is not illegal. However, there may be cases where this responded dramatically, with insults, with further phone calls and even death threats. The likelihood that the serious, is low. But they seem, nevertheless, authentic and highly unsettling. To bear in mind is that many scammers customers" are now "accustomed to, familiar with the mesh and defence, according to make a joke be parried matter-of-factly. And even the Stall you can save, experts say. Since the work of the men behind this Scam mesh with call centers in low-wage countries, is detrimental to this Trick, the profit margin.
The scammer baits
Nevertheless, the Scambaiting – the bait of cyber crooks become for some a kind of Hobby. It has the purpose to bring the scammers to waste time and energy on hopeless fraud, contact catch to be closed: be it procure to the satisfaction or information to law enforcement is helpful.
many cases of Scambaiting are documented for the Nigeria Connection. Operates since twenty years in advance cases of fraud with allegedly rich Prince or a lottery win. Under the pretext of the authenticity of the other check were the self-appointed fighter against the Scam, the scammers do certain things, and the photographically capture. In addition to a harmless Joke, there were also cases of humiliating sitting poses, for example, Nude on the toilet, or panels with phrases in foreign languages ("I'm an asshole") highly entertaining. Of course, these photos end up immediately in the network. This denunciation, however, except Eight, so just asked are often just the sidekick, the acting out of economic Hardship. And, of course, anyone with such pictures really helped.
security companies keep a low profile
security companies give questions about the topic covered. Symantec indicates that the request only on a blog post on the many years of cooperation with law enforcement agencies such as the FBI or the European Cyber Crime Center of Europol. Because it's not about individual scammers, but against a global fraud rings and botnets.
Private investigation actions are futile: for this reason alone, because the scammers usually sit in distant countries and concrete results of the investigations can hardly exploit. It remains the case that to delete the email, or dubious Call, simply hang up, the only sensible reaction.
exceptions confirm the rule: The Youtuber Kitboga deserves, in the meantime, his living with video, in which he slips into the role of grandmother Edna or hip valley girls Nevaeh, to make the scammer look stupid. He is not focused on Aggression, but peaceful tactics such as Comedy. Nevertheless, In a portrait with the magazine "Newsweek" he reveals how much he invested in his safety and the ease with which he prepared the Computer, work for the scammers are real, but of course, no personal data included. (Tages-Anzeiger.ch/Newsnet)
Created: 14.05.2019, 19:07 PM

 Hamas-Israel war: US begins construction of pier in Gaza
Hamas-Israel war: US begins construction of pier in Gaza Israel prepares to attack Rafah
Israel prepares to attack Rafah Indifference in European capitals, after Emmanuel Macron's speech at the Sorbonne
Indifference in European capitals, after Emmanuel Macron's speech at the Sorbonne Spain: what is Manos Limpias, the pseudo-union which denounced the wife of Pedro Sánchez?
Spain: what is Manos Limpias, the pseudo-union which denounced the wife of Pedro Sánchez?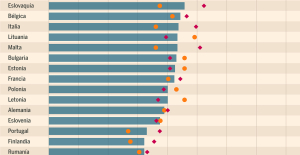 Spain is the country in the European Union with the most overqualified workers for their jobs
Spain is the country in the European Union with the most overqualified workers for their jobs Parvovirus alert, the “fifth disease” of children which has already caused the death of five babies in 2024
Parvovirus alert, the “fifth disease” of children which has already caused the death of five babies in 2024 Colorectal cancer: what to watch out for in those under 50
Colorectal cancer: what to watch out for in those under 50 H5N1 virus: traces detected in pasteurized milk in the United States
H5N1 virus: traces detected in pasteurized milk in the United States Private clinics announce a strike with “total suspension” of their activities, including emergencies, from June 3 to 5
Private clinics announce a strike with “total suspension” of their activities, including emergencies, from June 3 to 5 The Lagardère group wants to accentuate “synergies” with Vivendi, its new owner
The Lagardère group wants to accentuate “synergies” with Vivendi, its new owner The iconic tennis video game “Top Spin” returns after 13 years of absence
The iconic tennis video game “Top Spin” returns after 13 years of absence Three Stellantis automobile factories shut down due to supplier strike
Three Stellantis automobile factories shut down due to supplier strike A pre-Roman necropolis discovered in Italy during archaeological excavations
A pre-Roman necropolis discovered in Italy during archaeological excavations Searches in Guadeloupe for an investigation into the memorial dedicated to the history of slavery
Searches in Guadeloupe for an investigation into the memorial dedicated to the history of slavery Aya Nakamura in Olympic form a few hours before the Flames ceremony
Aya Nakamura in Olympic form a few hours before the Flames ceremony Psychiatrist Raphaël Gaillard elected to the French Academy
Psychiatrist Raphaël Gaillard elected to the French Academy Skoda Kodiaq 2024: a 'beast' plug-in hybrid SUV
Skoda Kodiaq 2024: a 'beast' plug-in hybrid SUV Tesla launches a new Model Y with 600 km of autonomy at a "more accessible price"
Tesla launches a new Model Y with 600 km of autonomy at a "more accessible price" The 10 best-selling cars in March 2024 in Spain: sales fall due to Easter
The 10 best-selling cars in March 2024 in Spain: sales fall due to Easter A private jet company buys more than 100 flying cars
A private jet company buys more than 100 flying cars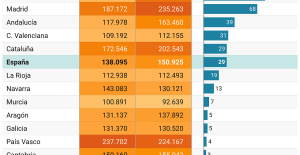 This is how housing prices have changed in Spain in the last decade
This is how housing prices have changed in Spain in the last decade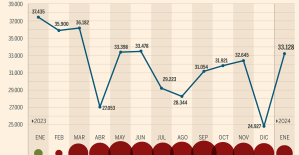 The home mortgage firm drops 10% in January and interest soars to 3.46%
The home mortgage firm drops 10% in January and interest soars to 3.46% The jewel of the Rocío de Nagüeles urbanization: a dream villa in Marbella
The jewel of the Rocío de Nagüeles urbanization: a dream villa in Marbella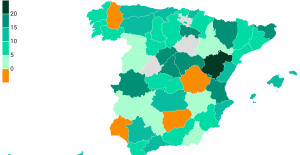 Rental prices grow by 7.3% in February: where does it go up and where does it go down?
Rental prices grow by 7.3% in February: where does it go up and where does it go down? “Deadly Europe”, “economic decline”, immigration… What to remember from Emmanuel Macron’s speech at the Sorbonne
“Deadly Europe”, “economic decline”, immigration… What to remember from Emmanuel Macron’s speech at the Sorbonne Sale of Biogaran: The Republicans write to Emmanuel Macron
Sale of Biogaran: The Republicans write to Emmanuel Macron Europeans: “All those who claim that we don’t need Europe are liars”, criticizes Bayrou
Europeans: “All those who claim that we don’t need Europe are liars”, criticizes Bayrou With the promise of a “real burst of authority”, Gabriel Attal provokes the ire of the opposition
With the promise of a “real burst of authority”, Gabriel Attal provokes the ire of the opposition These French cities that will boycott the World Cup in Qatar
These French cities that will boycott the World Cup in Qatar Judo: Blandine Pont European vice-champion
Judo: Blandine Pont European vice-champion Swimming: World Anti-Doping Agency appoints independent prosecutor in Chinese doping case
Swimming: World Anti-Doping Agency appoints independent prosecutor in Chinese doping case Water polo: everything you need to know about this sport
Water polo: everything you need to know about this sport Judo: Cédric Revol on the 3rd step of the European podium
Judo: Cédric Revol on the 3rd step of the European podium


















