The ratings in our Video category "Digital recipes" to show a clear image, no matter what our audience is and what is not. Interest solid push as far as possible, from the real-life proposals for a solution that quickly and precisely to the point.
This is not to say, however, that our readers go and the path of least resistance. On the contrary, The following Video met with very great interest, which explains how to maintain data sovereignty. Instead of all the images, photos and files upload is easy with a Cloud service provider and no longer have to worry, many are willing to operate for independence and self-determination a bit more effort.
So, you remain the master of your data
Just as important as the protection of personal data is the privacy. The following instructions are met with a good response, because it shows the users the different options: from small, hand-held handles that offer more security, up to the radical anonymity.
From moderate to paranoid: Four ways to protect yourself online
A Chance for more autonomy in the data storage, also thanks to the data protection basic regulation, which entered into effect in 2018. As a user, you do not need to beat yourself to the luck with the legal Details, but can benefit from the new opportunities. The so-called data portability makes it possible to export data for some services. According to the Motto: What you have you have.
the data take – how it works
But what to do if the child has fallen in spite of everything, in the fountain, and important digital treasures have come in spite of the precautions lost? Then the tips data help rescue, you may also preventative in the hope that it never comes so far.
to round off The last Chance for lost files
the measures for the protection of data and privacy, you should arm yourself against large and small errors in operating systems and application programs. The first Video of the year offers of help.
How to protect against security vulnerabilities
safety is a concern – pace of the second. Because optimization opportunities there are. Notoriously slow Wi-Fi ...
Wi-Fi with maximum speed
... and on the other hand, the operating system is on the one hand. Windows tends to known to be over the months and years of getting slower and slower. Fortunately, the digital decay is now no longer as bad as in previous versions. And there are effective methods with which to power the PC back legs.
So, Windows will again soon
Also in the Smartphone-use our audience hand like it. The Video describes here, how to turn your phone into an all-purpose tool, with the missing objects, houses, objects weighs, according to the strengths and (not in the Video, but also fascinating) the smart phone as a Geiger counter uses.
With these Apps, the Smartphone measures correctly
A nerve, we have made obviously with the tips to Powerpoint, or maybe you would have to say against Powerpoint. Because boring presentations start at the Software. The Alternatives are bound to raise creative ideas for presentations and lectures, and to encourage them to commit new paths for the image support.
As the film hell to escape
Finally, our readers are not averse to the entertainment. But also because you should be as self-determined, as is with the means of modern technology at all possible. That means television and video viewing, disappear as independent as possible of the transmission schedules of the television stations and the media libraries from which the shipments exactly when you would finally have time to watch it...
these are the best TV Apps (editorial Tamedia)
Created: 31.12.2018, 14:57 PM

 United States: divided on the question of presidential immunity, the Supreme Court offers respite to Trump
United States: divided on the question of presidential immunity, the Supreme Court offers respite to Trump Maurizio Molinari: “the Scurati affair, a European injury”
Maurizio Molinari: “the Scurati affair, a European injury” Hamas-Israel war: US begins construction of pier in Gaza
Hamas-Israel war: US begins construction of pier in Gaza Israel prepares to attack Rafah
Israel prepares to attack Rafah First three cases of “native” cholera confirmed in Mayotte
First three cases of “native” cholera confirmed in Mayotte Meningitis: compulsory vaccination for babies will be extended in 2025
Meningitis: compulsory vaccination for babies will be extended in 2025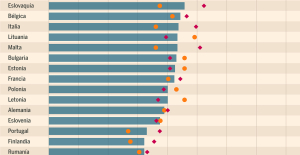 Spain is the country in the European Union with the most overqualified workers for their jobs
Spain is the country in the European Union with the most overqualified workers for their jobs Parvovirus alert, the “fifth disease” of children which has already caused the death of five babies in 2024
Parvovirus alert, the “fifth disease” of children which has already caused the death of five babies in 2024 Falling wings of the Moulin Rouge: who will pay for the repairs?
Falling wings of the Moulin Rouge: who will pay for the repairs? “You don’t sell a company like that”: Roland Lescure “annoyed” by the prospect of a sale of Biogaran
“You don’t sell a company like that”: Roland Lescure “annoyed” by the prospect of a sale of Biogaran Insults, threats of suicide, violence... Attacks by France Travail agents will continue to soar in 2023
Insults, threats of suicide, violence... Attacks by France Travail agents will continue to soar in 2023 TotalEnergies boss plans primary listing in New York
TotalEnergies boss plans primary listing in New York La Pléiade arrives... in Pléiade
La Pléiade arrives... in Pléiade In Japan, an animation studio bets on its creators suffering from autism spectrum disorders
In Japan, an animation studio bets on its creators suffering from autism spectrum disorders Terry Gilliam, hero of the Annecy Festival, with Vice-Versa 2 and Garfield
Terry Gilliam, hero of the Annecy Festival, with Vice-Versa 2 and Garfield François Hollande, Stéphane Bern and Amélie Nothomb, heroes of one evening on the beach of the Cannes Film Festival
François Hollande, Stéphane Bern and Amélie Nothomb, heroes of one evening on the beach of the Cannes Film Festival Skoda Kodiaq 2024: a 'beast' plug-in hybrid SUV
Skoda Kodiaq 2024: a 'beast' plug-in hybrid SUV Tesla launches a new Model Y with 600 km of autonomy at a "more accessible price"
Tesla launches a new Model Y with 600 km of autonomy at a "more accessible price" The 10 best-selling cars in March 2024 in Spain: sales fall due to Easter
The 10 best-selling cars in March 2024 in Spain: sales fall due to Easter A private jet company buys more than 100 flying cars
A private jet company buys more than 100 flying cars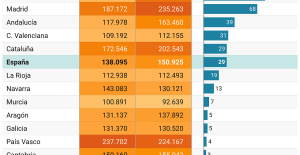 This is how housing prices have changed in Spain in the last decade
This is how housing prices have changed in Spain in the last decade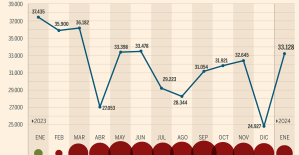 The home mortgage firm drops 10% in January and interest soars to 3.46%
The home mortgage firm drops 10% in January and interest soars to 3.46% The jewel of the Rocío de Nagüeles urbanization: a dream villa in Marbella
The jewel of the Rocío de Nagüeles urbanization: a dream villa in Marbella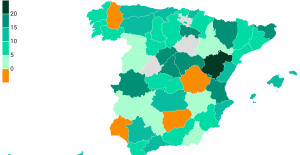 Rental prices grow by 7.3% in February: where does it go up and where does it go down?
Rental prices grow by 7.3% in February: where does it go up and where does it go down? Even on a mission for NATO, the Charles-de-Gaulle remains under French control, Lecornu responds to Mélenchon
Even on a mission for NATO, the Charles-de-Gaulle remains under French control, Lecornu responds to Mélenchon “Deadly Europe”, “economic decline”, immigration… What to remember from Emmanuel Macron’s speech at the Sorbonne
“Deadly Europe”, “economic decline”, immigration… What to remember from Emmanuel Macron’s speech at the Sorbonne Sale of Biogaran: The Republicans write to Emmanuel Macron
Sale of Biogaran: The Republicans write to Emmanuel Macron Europeans: “All those who claim that we don’t need Europe are liars”, criticizes Bayrou
Europeans: “All those who claim that we don’t need Europe are liars”, criticizes Bayrou These French cities that will boycott the World Cup in Qatar
These French cities that will boycott the World Cup in Qatar Medicine, family of athletes, New Zealand…, discovering Manae Feleu, the captain of the Bleues
Medicine, family of athletes, New Zealand…, discovering Manae Feleu, the captain of the Bleues Football: OM wants to extend Leonardo Balerdi
Football: OM wants to extend Leonardo Balerdi Six Nations F: France-England shatters the attendance record for women’s rugby in France
Six Nations F: France-England shatters the attendance record for women’s rugby in France Judo: eliminated in the 2nd round of the European Championships, Alpha Djalo in full doubt
Judo: eliminated in the 2nd round of the European Championships, Alpha Djalo in full doubt