this summer died with 93 years, one of the great computer pioneers. With its invention, we have to do day in and day out, whether it is on your Computer, or mobile phone. However, unlike, for example, Douglas Engelbart or Tim Berners Lee, the fathers of the mouse and of the World Wide Web, the creation of Fernando Corbató today, a mixed reputation: it plays a Central role in the security of our data. But it is also troublesome and time-consuming. Also Corbató has been at odds before his death with her. "It's kind of a nightmare," he said in 2014 in an Interview with the Wall Street Journal: "I don't know how someone will all of this pass is to memorize words."
Fernando Corbató was involved in the 1960s at mit in Massachusetts to a multi-user system. There's a larger group of users had access to the Terminals and it was possible to also store personal data, it needed a safety mechanism. A password to protect, there was an obvious solution, had declared Corbató, 2012, the magazine "Wired".
the password was invented – the developers in an Interview from 1963 with information on the state of technical development.
The solution has held up over the decades. However, in this time, the big mutant computer Terminals to Personal computers and mobile devices. Our personal data are scattered in the Internet to dozens or hundreds of servers. And the biggest risk is not that a curious colleague takes a look at something that's none of his business. Today is cyber try criminal gangs to steal data, to misuse and to silver. And again, it shows that the access data are protected in the case of the Internet companies are bad. The weekend has become known that in the case of the software manufacturer Adobe were the data could be stolen to 7.5 million subscribers to the Creative Cloud service.
easily Chop
These fundamental problems were already at the very beginning: Even at mit, there were gaps in security and "Hacker". "Wired" tells the story of how Allan Scherr, then a doctoral student, required more computation time. He obtained by requesting a printout of all the passwords, and received – and with other accounts, also of the laboratory heads, could log in.
The drawbacks, in Spite of the password. We hold today, however, we can use password Manager and longer and longer and more complex passwords. As an additional Element, the Two-factor authentication has come to this. When Logging on through a one-time will be added to the Code. This increases the security significantly: A Hacker must acquire only the Login-data, but also this second factor, in a foreign account to break in. However, the effort for the user and the potential for error is greater. If you use the phone for the second factor, then the loss of the device means that you can get at its data.
Biometric Sensors
the trick, of Course, there are efforts, this relic from the early days of computer networking to replace. A relief to have brought in biometric systems in 2013 with the iPhone 5S to the masses. The fingerprint sensor, or face scan eliminates the need to Type in the cell phone passcode. He also unlocks the device password Manager on the mobile or Computer, what makes the Log less of a hassle.
How to beat a fingerprint scanner.
As a replacement for a password biometric systems are not suitable. Because biometric features can "steal": in 2007, managed the Chaos Computer Club, to outwit the fingerprint sensor at a supermarket checkout. Face scanners can be duped by masks from the 3-D-printer – and you also grant to twins or very similar looking family members access. A second Problem is that the physical characteristics change over time, and a detection is never a hundred percent, but only within certain tolerances.
The digital ID as a solution?
The SwissID don't want to get rid of the password, but it is simplified in that the same Login can be used on a protected manner in the case of many services. This is can be used as a digital identity card that is issued once, everywhere. This sounds straightforward, in practice, but hooks and eyes: It is a tug-of-war over whether such Internet-card is to be issued by private companies or the state.
And such an ID would make users very clear to many of the systems identified. With the today usual separate Logins, users can keep their Online identities separate, and some of the services even with a Pseudonym-Login use. And of course, the SwissID would be a national solution in the global Internet.
A password-less future, the Fido Alliance is aiming for. To your Google, Mastercard and Visa, Microsoft and Samsung are now involved. She stands behind the Fido2-Standard that you log in with a physical key: This can be a kind of USB Stick that you plugged in his Computer, Tablet or Smartphone. The key could also be in a smart watch or other Wearable placed.
Microsoft has installed Fido2 since may of this year, in its web sites and in Windows Hello. Users can log in instead of password with a USB security key many of the services of the group. And that actually works – how exactly, we show in this Video:
The key we have used is a Yubikey 5, the for about 45 Swiss francs, for example, in the case of Yubikey.ch is available. Windows 10 and Android can also be used as a security key, so that it can take you no Extra Hardware.
Until Fido2 on a broad Basis in the Internet has been established, it will take a few more years. But all the same, The password-Chaos is likely to ease in the long term.
Created: 29.10.2019, 18:39 PM

 Germany: Man armed with machete enters university library and threatens staff
Germany: Man armed with machete enters university library and threatens staff His body naturally produces alcohol, he is acquitted after a drunk driving conviction
His body naturally produces alcohol, he is acquitted after a drunk driving conviction Who is David Pecker, the first key witness in Donald Trump's trial?
Who is David Pecker, the first key witness in Donald Trump's trial? What does the law on the expulsion of migrants to Rwanda adopted by the British Parliament contain?
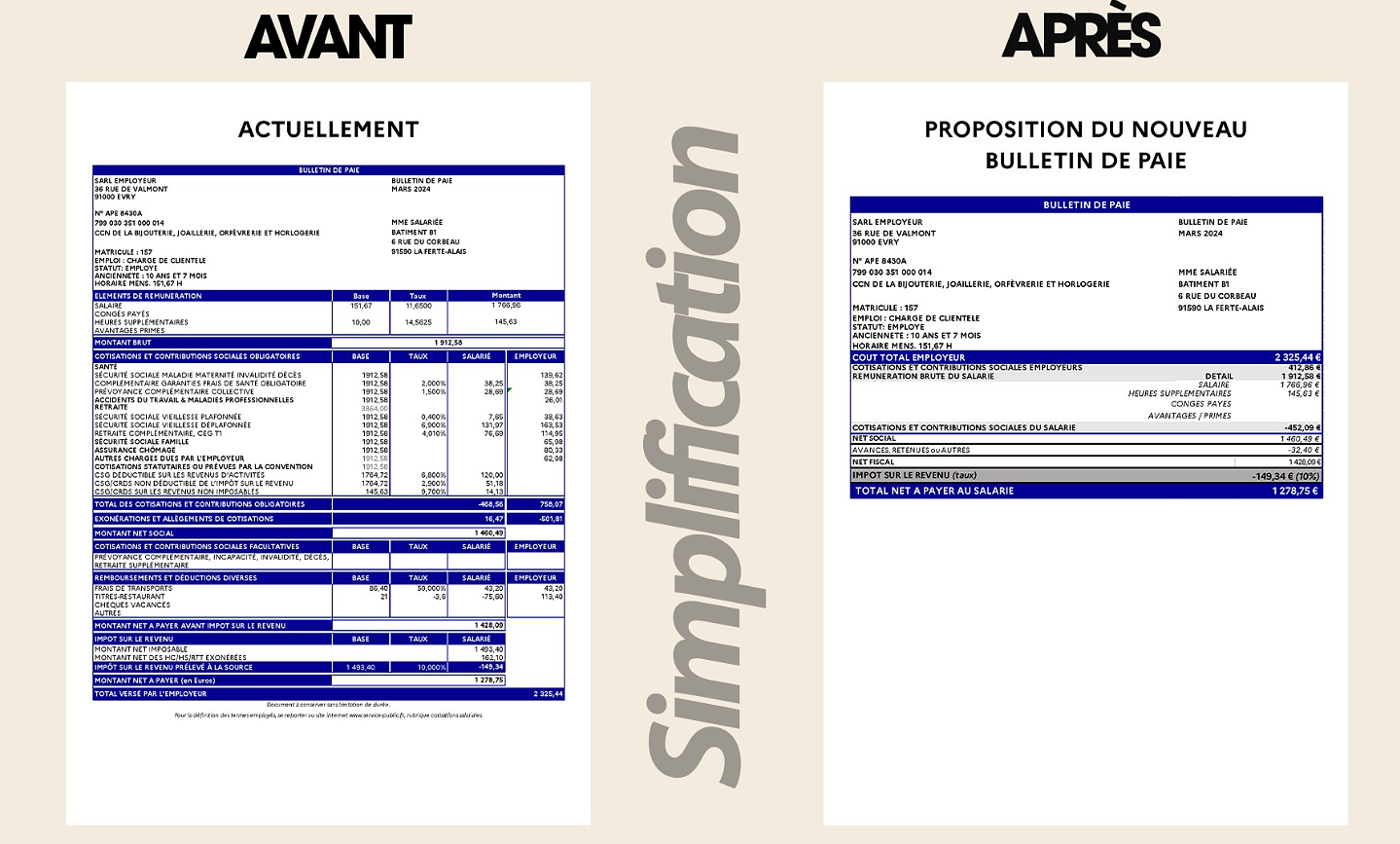
What does the law on the expulsion of migrants to Rwanda adopted by the British Parliament contain?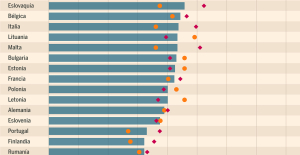 Spain is the country in the European Union with the most overqualified workers for their jobs
Spain is the country in the European Union with the most overqualified workers for their jobs Parvovirus alert, the “fifth disease” of children which has already caused the death of five babies in 2024
Parvovirus alert, the “fifth disease” of children which has already caused the death of five babies in 2024 Colorectal cancer: what to watch out for in those under 50
Colorectal cancer: what to watch out for in those under 50 H5N1 virus: traces detected in pasteurized milk in the United States
H5N1 virus: traces detected in pasteurized milk in the United States Insurance: SFAM, subsidiary of Indexia, placed in compulsory liquidation
Insurance: SFAM, subsidiary of Indexia, placed in compulsory liquidation Under pressure from Brussels, TikTok deactivates the controversial mechanisms of its TikTok Lite application
Under pressure from Brussels, TikTok deactivates the controversial mechanisms of its TikTok Lite application “I can’t help but panic”: these passengers worried about incidents on Boeing
“I can’t help but panic”: these passengers worried about incidents on Boeing “I’m interested in knowing where the money that the State takes from me goes”: Bruno Le Maire’s strange pay slip sparks controversy
“I’m interested in knowing where the money that the State takes from me goes”: Bruno Le Maire’s strange pay slip sparks controversy 25 years later, the actors of Blair Witch Project are still demanding money to match the film's record profits
25 years later, the actors of Blair Witch Project are still demanding money to match the film's record profits At La Scala, Mathilde Charbonneaux is Madame M., Jacqueline Maillan
At La Scala, Mathilde Charbonneaux is Madame M., Jacqueline Maillan Deprived of Hollywood and Western music, Russia gives in to the charms of K-pop and manga
Deprived of Hollywood and Western music, Russia gives in to the charms of K-pop and manga Exhibition: Toni Grand, the incredible odyssey of a sculptural thinker
Exhibition: Toni Grand, the incredible odyssey of a sculptural thinker Skoda Kodiaq 2024: a 'beast' plug-in hybrid SUV
Skoda Kodiaq 2024: a 'beast' plug-in hybrid SUV Tesla launches a new Model Y with 600 km of autonomy at a "more accessible price"
Tesla launches a new Model Y with 600 km of autonomy at a "more accessible price" The 10 best-selling cars in March 2024 in Spain: sales fall due to Easter
The 10 best-selling cars in March 2024 in Spain: sales fall due to Easter A private jet company buys more than 100 flying cars
A private jet company buys more than 100 flying cars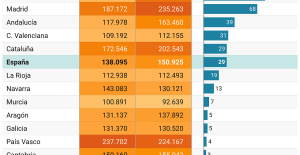 This is how housing prices have changed in Spain in the last decade
This is how housing prices have changed in Spain in the last decade The home mortgage firm drops 10% in January and interest soars to 3.46%
The home mortgage firm drops 10% in January and interest soars to 3.46% The jewel of the Rocío de Nagüeles urbanization: a dream villa in Marbella
The jewel of the Rocío de Nagüeles urbanization: a dream villa in Marbella Rental prices grow by 7.3% in February: where does it go up and where does it go down?
Rental prices grow by 7.3% in February: where does it go up and where does it go down? Sale of Biogaran: The Republicans write to Emmanuel Macron
Sale of Biogaran: The Republicans write to Emmanuel Macron Europeans: “All those who claim that we don’t need Europe are liars”, criticizes Bayrou
Europeans: “All those who claim that we don’t need Europe are liars”, criticizes Bayrou With the promise of a “real burst of authority”, Gabriel Attal provokes the ire of the opposition
With the promise of a “real burst of authority”, Gabriel Attal provokes the ire of the opposition Europeans: the schedule of debates to follow between now and June 9
Europeans: the schedule of debates to follow between now and June 9 These French cities that will boycott the World Cup in Qatar
These French cities that will boycott the World Cup in Qatar Hand: Montpellier crushes Kiel and continues to dream of the Champions League
Hand: Montpellier crushes Kiel and continues to dream of the Champions League OM-Nice: a spectacular derby, Niçois timid despite their numerical superiority...The tops and the flops
OM-Nice: a spectacular derby, Niçois timid despite their numerical superiority...The tops and the flops Tennis: 1000 matches and 10 notable encounters by Richard Gasquet
Tennis: 1000 matches and 10 notable encounters by Richard Gasquet Tennis: first victory of the season on clay for Osaka in Madrid
Tennis: first victory of the season on clay for Osaka in Madrid