But paying includes no penalties and denying are almost suicidal for most businesses, particularly the small and medium-sized. The consequences may also be dire for the country . Recent high-profile extortive strikes led to runs on East Coast gas channels and jeopardized meat provides .
The problem has left people officials thinking about the best way to react. In a first step, bipartisan legislation in the functions would mandate immediate national reporting of ransomware strikes to aid answer, help identify the writers as well as recover ransoms, since the FBI did with the majority of the 4.4 million who Colonial Pipeline lately paid.
Without further action shortly, however, specialists state ransoms will continue to innovate, funding better offender intelligence-gathering and resources that just worsen the worldwide crime wave.
President Joe Biden obtained no assurances from Russian President Vladimir Putin at Geneva last week which cybercriminals supporting the strikes will not continue to enjoy safe haven in Russia. At the minimum, Putin's safety providers endure them. At worstthey are working together.
However, I really don't understand if Congress or the president has been" in favor,'' she explained.
And as Goldstein educated lawmakers, paying does not guarantee you will receive your information back or sensitive stolen documents won't wind up available in darknet offender forums. Even if the ransomware crooks keep their sentence, you're going to be funding their next round of strikes. And you might just get hit .
Back in Aprilthe then-top federal security official at the Justice Department, John Demers, was lukewarm toward prohibiting obligations, saying it may put"us at a more adversarial posture vis-à-vis the sufferers, which isn't where we would like to be."
Maybe most vehement about a payment prohibit are individuals who understand ransomware offenders finest -- cybersecurity threat responders.
"Finally, the terrorists ceased kidnapping people since they understood they were not likely to get compensated," explained Adrian Nish, hazard intelligence leader in BAE Systems.
U.S. law prohibits material support for terrorists, however, the Justice Department at 2015 waived the danger of criminal prosecution for taxpayers who cover terrorist ransoms.
Some ransomware sufferers have taken principled stands against obligations, the individual costs be damned.
Ireland, also, refused to negotiate if its federal health care service was struck last month.
Five months on, healthcare information technology from the country of 5 million stays badly hobbled. Cancer therapies are only partially revived, email support patchy, electronic patient records mainly inaccessible. Individuals jam emergency rooms because of laboratory and diagnostic evaluations because their primary-care physicians can not dictate them. As of Thursday, 42 percent of the system 4,000 pc servers still hadn't been decrypted.
The offenders turned over the applications decryption key per week after the assault -- after an odd offer from the Russian Embassy to"assistance with the analysis" -- but that the restoration was a painful slog.
"A decryption key isn't a magic wand or change that may suddenly reverse the harm," explained Brian Honan, a leading Irish cybersecurity advisor. Every device recovered must be analyzed to make sure it is infection-free.
Data indicate that many ransomware victims cover. The agency Hiscox says just over 58 percent of its affected customers cover, while contributing cyber insurance broker Marsh McLennan set the figure at approximately 60% because of its affected U.S. and Canadian customers.
But paying does not promise anything near complete recovery. Normally, ransom-payers gained back only 65 percent of the encoded data, leaving over a third inaccessible, whereas 29 percent said they obtained just half of their information ago, the cybersecurity company Sophos discovered in a poll of 5,400 IT decision-makers in 30 nations.
In a poll of almost 1,300 security specialists, Cybereason discovered that 4 in five companies that decided to pay ransoms endured another ransomware assault.
This calculus however, deep-pocketed companies with insurance coverage tend to cover up.
Colonial Pipeline almost instantly paid to find fuel flowing back into the U.S. East Coast -- prior to deciding whether its data copies were strong enough to prevent payment. Afterwards, meat-processing goliath JBS paid $11 million to prevent potentially interrupting U.S. beef provide, though its information copies also demonstrated sufficient to receive its crops back online before severe harm.
It is not apparent if concern about stolen information being dumped on the web determined the choice of company to pay.
Colonial wouldn't say if anxieties of this 100 gigabytes of stolen information end up in the public factored into the decision by CEO Joseph Blount to cover. JBS spokesman Cameron Bruett stated"our investigation showed no firm data was exfiltrated." He wouldn't say if the offenders maintained within their ransom note to possess stolen information.
Irish governments were fully conscious of the dangers. The offenders claim to possess murdered 700 gigabytes of information. As yet, it hasn't surfaced on the web.
Public exposure of these data may result in lost or lawsuits investor confidence, making it manna for offenders. 1 ransomware gang trying to extort a significant U.S. business released a nude photograph of the chief executive adult son on its own escape site a week.
Bloomberg News reported that CNA Insurance declared $40 million into ransomware offenders in March.
Recognizing a lack of assistance for a ransom prohibit, Senate Intelligence Committee Chairman Mark Warner, D-Va., along with other lawmakers need at least to induce increased transparency from ransomware sufferers, who often do not report attacks.
They're drafting a bill to create the coverage of breaches and ransom payments required.
But that will not shield unprepared victims from possibly going bankrupt if they do not pay. For this, various proposals are put forward to offer financial aid.
The Senate this month approved laws that could set a particular cyber response and restoration fund to offer immediate support to the vulnerable public and private organizations struck by significant cyberattacks and breaches.

 His body naturally produces alcohol, he is acquitted after a drunk driving conviction
His body naturally produces alcohol, he is acquitted after a drunk driving conviction Who is David Pecker, the first key witness in Donald Trump's trial?
Who is David Pecker, the first key witness in Donald Trump's trial? What does the law on the expulsion of migrants to Rwanda adopted by the British Parliament contain?
What does the law on the expulsion of migrants to Rwanda adopted by the British Parliament contain? The shadow of Chinese espionage hangs over Westminster
The shadow of Chinese espionage hangs over Westminster Colorectal cancer: what to watch out for in those under 50
Colorectal cancer: what to watch out for in those under 50 H5N1 virus: traces detected in pasteurized milk in the United States
H5N1 virus: traces detected in pasteurized milk in the United States What High Blood Pressure Does to Your Body (And Why It Should Be Treated)
What High Blood Pressure Does to Your Body (And Why It Should Be Treated) Vaccination in France has progressed in 2023, rejoices Public Health France
Vaccination in France has progressed in 2023, rejoices Public Health France The right deplores a “dismal agreement” on the end of careers at the SNCF
The right deplores a “dismal agreement” on the end of careers at the SNCF The United States pushes TikTok towards the exit
The United States pushes TikTok towards the exit Air traffic controllers strike: 75% of flights canceled at Orly on Thursday, 65% at Roissy and Marseille
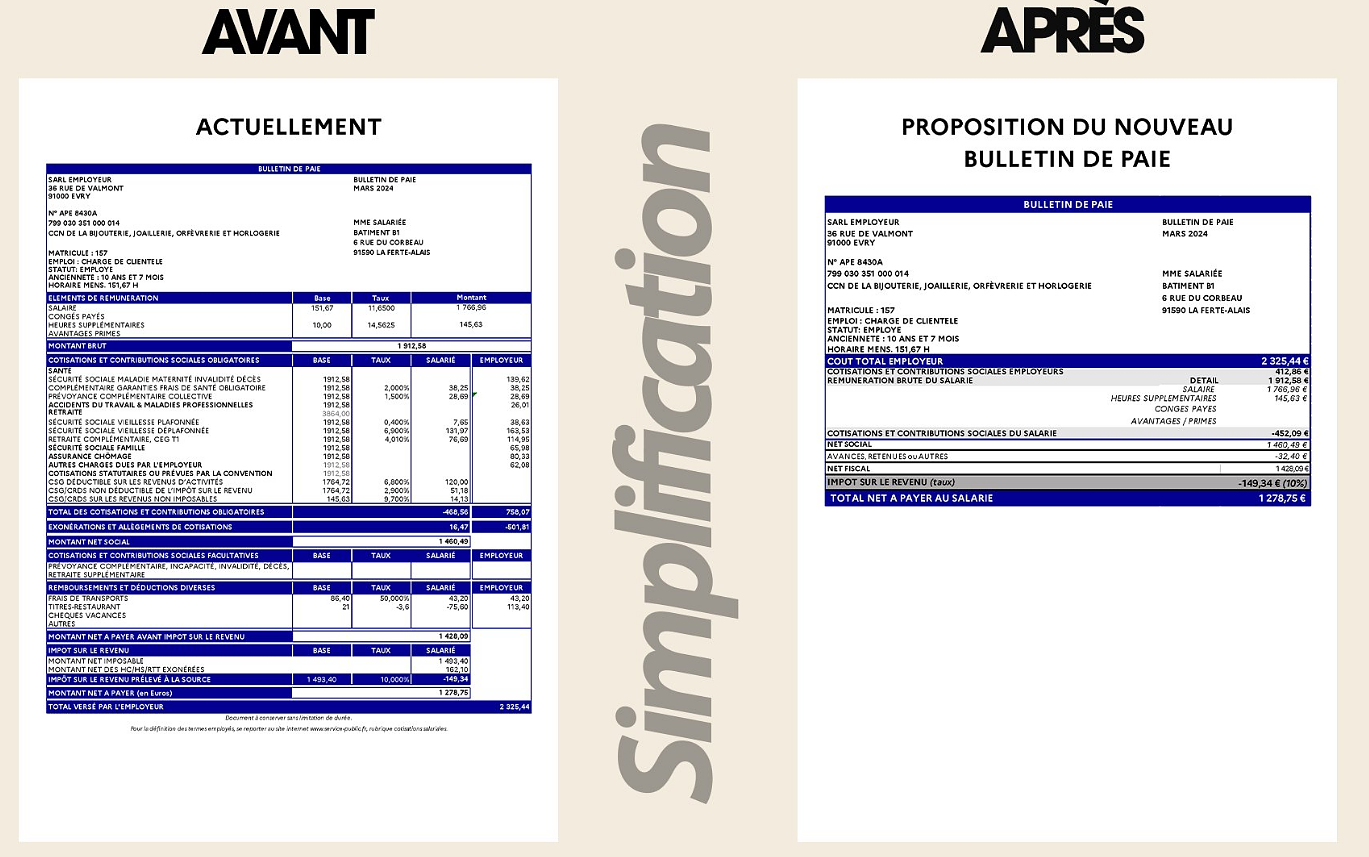
Air traffic controllers strike: 75% of flights canceled at Orly on Thursday, 65% at Roissy and Marseille This is what your pay slip could look like tomorrow according to Bruno Le Maire
This is what your pay slip could look like tomorrow according to Bruno Le Maire Sky Dome 2123, Challengers, Back to Black... Films to watch or avoid this week
Sky Dome 2123, Challengers, Back to Black... Films to watch or avoid this week The standoff between the organizers of Vieilles Charrues and the elected officials of Carhaix threatens the festival
The standoff between the organizers of Vieilles Charrues and the elected officials of Carhaix threatens the festival Strasbourg inaugurates a year of celebrations and debates as World Book Capital
Strasbourg inaugurates a year of celebrations and debates as World Book Capital Kendji Girac is “out of the woods” after his gunshot wound to the chest
Kendji Girac is “out of the woods” after his gunshot wound to the chest Skoda Kodiaq 2024: a 'beast' plug-in hybrid SUV
Skoda Kodiaq 2024: a 'beast' plug-in hybrid SUV Tesla launches a new Model Y with 600 km of autonomy at a "more accessible price"
Tesla launches a new Model Y with 600 km of autonomy at a "more accessible price" The 10 best-selling cars in March 2024 in Spain: sales fall due to Easter
The 10 best-selling cars in March 2024 in Spain: sales fall due to Easter A private jet company buys more than 100 flying cars
A private jet company buys more than 100 flying cars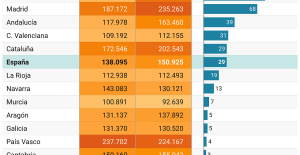 This is how housing prices have changed in Spain in the last decade
This is how housing prices have changed in Spain in the last decade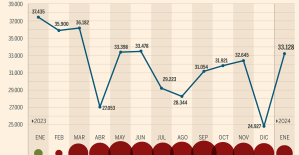 The home mortgage firm drops 10% in January and interest soars to 3.46%
The home mortgage firm drops 10% in January and interest soars to 3.46% The jewel of the Rocío de Nagüeles urbanization: a dream villa in Marbella
The jewel of the Rocío de Nagüeles urbanization: a dream villa in Marbella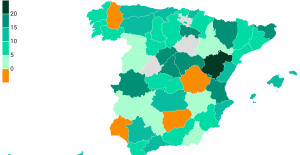 Rental prices grow by 7.3% in February: where does it go up and where does it go down?
Rental prices grow by 7.3% in February: where does it go up and where does it go down? Europeans: “All those who claim that we don’t need Europe are liars”, criticizes Bayrou
Europeans: “All those who claim that we don’t need Europe are liars”, criticizes Bayrou With the promise of a “real burst of authority”, Gabriel Attal provokes the ire of the opposition
With the promise of a “real burst of authority”, Gabriel Attal provokes the ire of the opposition Europeans: the schedule of debates to follow between now and June 9
Europeans: the schedule of debates to follow between now and June 9 Europeans: “In France, there is a left and there is a right,” assures Bellamy
Europeans: “In France, there is a left and there is a right,” assures Bellamy These French cities that will boycott the World Cup in Qatar
These French cities that will boycott the World Cup in Qatar NBA: the Wolves escape against the Suns, Indiana unfolds and the Clippers defeated
NBA: the Wolves escape against the Suns, Indiana unfolds and the Clippers defeated Real Madrid: what position will Mbappé play? The answer is known
Real Madrid: what position will Mbappé play? The answer is known Cycling: Quintana will appear at the Giro
Cycling: Quintana will appear at the Giro Premier League: “The team has given up”, notes Mauricio Pochettino after Arsenal’s card
Premier League: “The team has given up”, notes Mauricio Pochettino after Arsenal’s card