A gritty skræmbillede pops up on Morten Brok computer.
On a heavily pixelated image one can feel the mandsperson dressed in blue shirt and gray cap. He's looking into the computer, and it does not seem to affect him, that he is being filmed. Probably he knows it not at all.
Morten has just hacked his victim.
On a daily basis, he works at IT-the company is Progressive in Aarhus. For more than 15 years, he has worked with it security and recent years, the threat from hackers has exploded in connection with the fact that cybercrime has become a billion business.
According to a statement made by the international provider of antivirusløsninger, Bitdefender, earned cyber criminals alone in 2017 more than five billion dollars to infect computers with ransomewhere.
Here it takes the hackers a company or individuals ' computers hostage and encrypts the files on the system, so they are locked for the user. Only when a ransom is paid, they get the code to unlock the computer again.
In the past year was a victim in a minute attacked by hackers with ransomware, according to Bitdefenders data.
the Article continues under the picture...
In may 2017 was more than 57,000 computers in an instant hit of Wannacry-attack, where a hackergruppe locked the computers and demanded a ransom of more tusindekroner paid in Bitcoins to unlock the computers up again. Screenshot
Hacked in few seconds
Morten keys a command on his keyboard. With one being the picture on his computer screen razor sharp, and it becomes clear that it is Extra the Magazine's journalist, who stands in front of the computer at the other end.
In the few seconds our computer has been hacked, and Morten can now see everything we do on the computer. Not only in front of the webcam, but also what I write on the keyboard, and the files that are stored on the hard disk.
He can aflure our passwords, look for upcoming articles or pictures from the just ended christmas.
The only tools Morten Brok used is a droneantenne to about 250 crowns, a free computer program - called a python script - a computer with the operating system Linux, as well as a server somewhere out in cyberspace.
I just hacked your computer through your wireless keyboard. I have shot a back door into your computer and disabled your antivirus software from. I have used a modified droneantenne, so that it can communicate with wireless devices like your keyboard, explains Morten Brok.
- The here most can learn if they have a bit of technical skill, and bother to familiarize themselves with the software. Everything is accessible through simple searches on for example Youtube and Google.
Since the appointment of Morten Brok shows how easily he forced himself access to the Ekstra computer, it is clear that the vast majority would be vulnerable to just this type of hacker attacks.
On morten's computer screen pops button a hundred wireless keyboards, mouse, alarm systems and much more. They are all located within a few hundred metre radius of the droneantennen.
In principle, I could attack all the computers that are hooked up to these devices. It is computers that are located all around the businesses housed in the building we are in now, he says.
According to Morten Brok is the vast majority of wireless keyboards sensitive to the type of attack he just performed at Ekstra equipment.
Among other popular models from Logitech, Microsoft and HP, there are thousands of Danish homes and businesses.
Since the hacker attack called 'mousejack' the first time was publicly known in 2016, promised the producers that they would update their equipment, so they were no longer vulnerable to hackertypen.
But the Logitech keyboard Extra Leaf use, is still vulnerable and hundreds of other devices in the office building in the outskirts of Aarhus, where we meet Morten Brok.
- I could put myself outside the Christiansborg palace, in front of Danske Bank's headquarters or an ex-girlfriend apartment with a directional antenna, and see if they were in vulnerable wireless devices, I could hack. This is very serious.
- The only way you can effectively protect yourself against this type of attack is to buy an 'old-fashioned' mouse and keyboard with wire.
How to you ensure yourself against the attacker
Hackers and malicious programs exploit security vulnerabilities in the apps, programs and operating systems. Vulnerabilities be closed on a continuous basis by the providers in connection with updates. Therefore, it is important to update them as soon as possible. In particular, web browsers such as. Chrome, Internet Explorer and Fire Fox is sensitive.
You can't be sure that an email comes from that sender. Links in emails may direct you to other locations, than it immediately shows. Therefore, please be cautious about clicking on links or follow the instructions in the e-mails you get sent unsolicited. You also should not open attachments in emails you are sent unsolicited.
Use long, complex and unpredictable passwords with both uppercase and lowercase letters as well as numbers. Use different passwords on different devices and services. The places where you have the option of two-step access control, you should use this. A password should be at least eight characters long.
Scammers may copy the look from the well-known web sites to try to, in general, you your information. Double check therefore the url before you enter sensitive personal information on svindelsiden ‘skat-dk.com’ that to perfection resembles its its official website tax.dk.
Look for ‘https’ before you fill in the forms with credit card information or sensitive personal information. The small ‘s’ in the browser ensures that no one outside can see the information you enter.
only Use secured WIFI-network. Do not Log on to the network without the code, since they can easily be misused to monitor you, collect your information about you or infect your devices with viruses.
Take backups of the things, you will not lose. Take advantage of offline resources as external hard drives or digital solutions from credible suppliers such as ‘Dropbox’ or ‘Google’. Thus, you ensure yourself from your stuff from becoming the victims of ‘ransomeware’ that takes your files hostage until you paid a ransom to the attackers.
Sources: the Council For Digital Security
read more Closethe Danes are ashamed
despite the fact that the cyber-criminals in 2017-earned billions to kidnap the computers and servers around the world, most crimes reported to the police at home.
In 2016, the police received 298 reviews of 'unauthorised access to computer information', while the figure for the first three quarters of 2017 is located at 232. It informs the national Police to Ekstra Bladet.
The low number of reviews may, according to the police commissioner at the National Cyber Crime Centre(NC3), Sonny Olesen, due to the fact that many do not report that they have been hacked.
- There are a number of different reasons that our numbers do not reflect the number of persons who are exposed to hacking out in reality. There is probably a large mørketal from people who do not know they have been hacked, while others are embarrassed or believe it is too small a thing to go to the police with, " explains Sonny Olesen and adds to the NC3 are seeing an increase in cyberkriminaliteten.
- If you are not a technical expert, it is difficult for the general it user to detect that his or her electronic devices has been abused to hunt down and extort a company or that video from your security cameras are directly sent out on obscure websites.

 His body naturally produces alcohol, he is acquitted after a drunk driving conviction
His body naturally produces alcohol, he is acquitted after a drunk driving conviction Who is David Pecker, the first key witness in Donald Trump's trial?
Who is David Pecker, the first key witness in Donald Trump's trial? What does the law on the expulsion of migrants to Rwanda adopted by the British Parliament contain?
What does the law on the expulsion of migrants to Rwanda adopted by the British Parliament contain? The shadow of Chinese espionage hangs over Westminster
The shadow of Chinese espionage hangs over Westminster Colorectal cancer: what to watch out for in those under 50
Colorectal cancer: what to watch out for in those under 50 H5N1 virus: traces detected in pasteurized milk in the United States
H5N1 virus: traces detected in pasteurized milk in the United States What High Blood Pressure Does to Your Body (And Why It Should Be Treated)
What High Blood Pressure Does to Your Body (And Why It Should Be Treated) Vaccination in France has progressed in 2023, rejoices Public Health France
Vaccination in France has progressed in 2023, rejoices Public Health France The right deplores a “dismal agreement” on the end of careers at the SNCF
The right deplores a “dismal agreement” on the end of careers at the SNCF The United States pushes TikTok towards the exit
The United States pushes TikTok towards the exit Air traffic controllers strike: 75% of flights canceled at Orly on Thursday, 65% at Roissy and Marseille
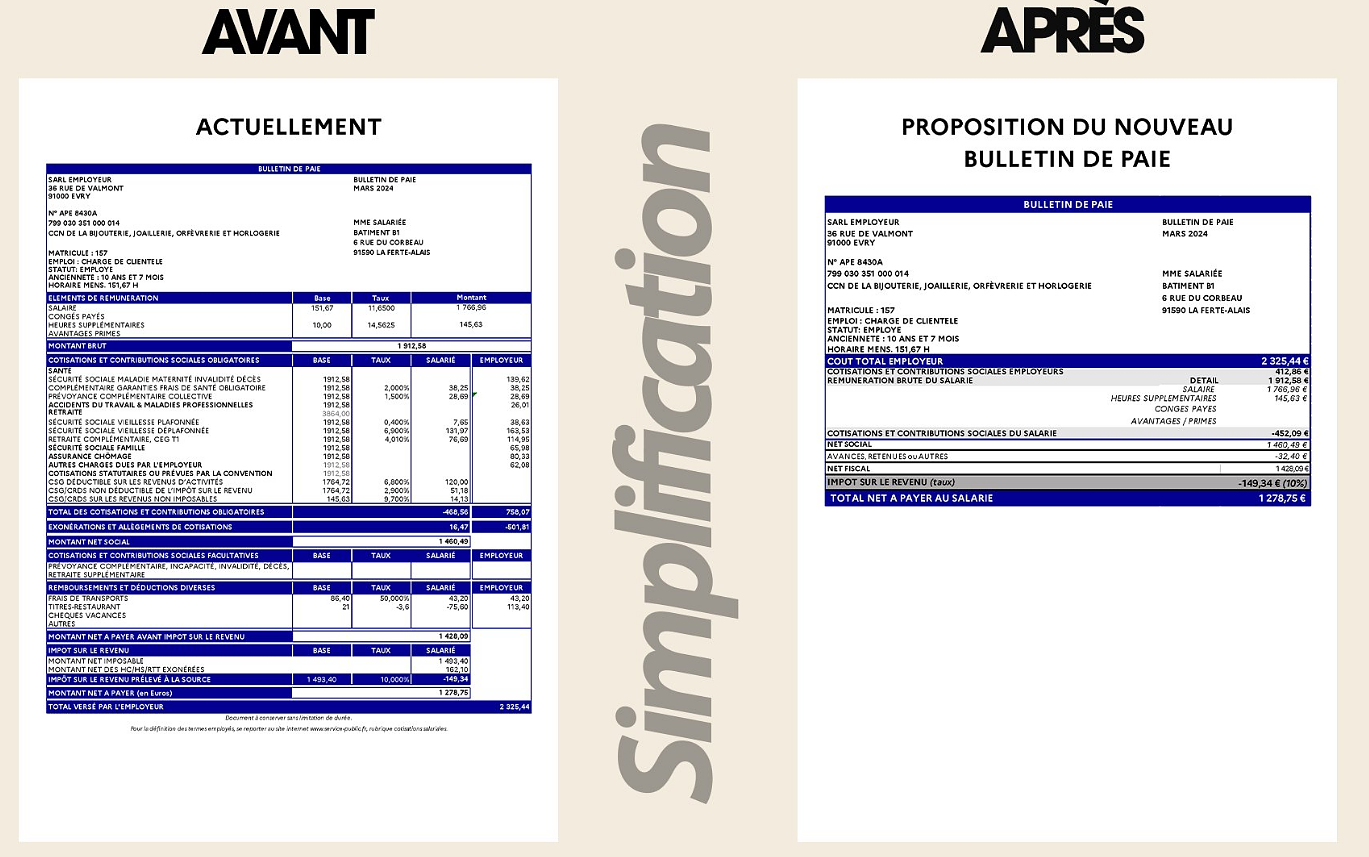
Air traffic controllers strike: 75% of flights canceled at Orly on Thursday, 65% at Roissy and Marseille This is what your pay slip could look like tomorrow according to Bruno Le Maire
This is what your pay slip could look like tomorrow according to Bruno Le Maire Sky Dome 2123, Challengers, Back to Black... Films to watch or avoid this week
Sky Dome 2123, Challengers, Back to Black... Films to watch or avoid this week The standoff between the organizers of Vieilles Charrues and the elected officials of Carhaix threatens the festival
The standoff between the organizers of Vieilles Charrues and the elected officials of Carhaix threatens the festival Strasbourg inaugurates a year of celebrations and debates as World Book Capital
Strasbourg inaugurates a year of celebrations and debates as World Book Capital Kendji Girac is “out of the woods” after his gunshot wound to the chest
Kendji Girac is “out of the woods” after his gunshot wound to the chest Skoda Kodiaq 2024: a 'beast' plug-in hybrid SUV
Skoda Kodiaq 2024: a 'beast' plug-in hybrid SUV Tesla launches a new Model Y with 600 km of autonomy at a "more accessible price"
Tesla launches a new Model Y with 600 km of autonomy at a "more accessible price" The 10 best-selling cars in March 2024 in Spain: sales fall due to Easter
The 10 best-selling cars in March 2024 in Spain: sales fall due to Easter A private jet company buys more than 100 flying cars
A private jet company buys more than 100 flying cars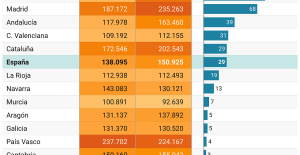 This is how housing prices have changed in Spain in the last decade
This is how housing prices have changed in Spain in the last decade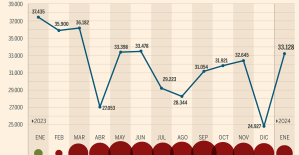 The home mortgage firm drops 10% in January and interest soars to 3.46%
The home mortgage firm drops 10% in January and interest soars to 3.46% The jewel of the Rocío de Nagüeles urbanization: a dream villa in Marbella
The jewel of the Rocío de Nagüeles urbanization: a dream villa in Marbella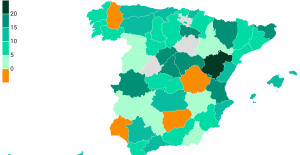 Rental prices grow by 7.3% in February: where does it go up and where does it go down?
Rental prices grow by 7.3% in February: where does it go up and where does it go down? Europeans: “All those who claim that we don’t need Europe are liars”, criticizes Bayrou
Europeans: “All those who claim that we don’t need Europe are liars”, criticizes Bayrou With the promise of a “real burst of authority”, Gabriel Attal provokes the ire of the opposition
With the promise of a “real burst of authority”, Gabriel Attal provokes the ire of the opposition Europeans: the schedule of debates to follow between now and June 9
Europeans: the schedule of debates to follow between now and June 9 Europeans: “In France, there is a left and there is a right,” assures Bellamy
Europeans: “In France, there is a left and there is a right,” assures Bellamy These French cities that will boycott the World Cup in Qatar
These French cities that will boycott the World Cup in Qatar NBA: the Wolves escape against the Suns, Indiana unfolds and the Clippers defeated
NBA: the Wolves escape against the Suns, Indiana unfolds and the Clippers defeated Real Madrid: what position will Mbappé play? The answer is known
Real Madrid: what position will Mbappé play? The answer is known Cycling: Quintana will appear at the Giro
Cycling: Quintana will appear at the Giro Premier League: “The team has given up”, notes Mauricio Pochettino after Arsenal’s card
Premier League: “The team has given up”, notes Mauricio Pochettino after Arsenal’s card