Asus has been the victim of an attack. Attackers have managed, apparently, in the Server, break in and malicious software in clients downloads to infiltrate. Via the automatic Update function this Software was distributed to hundreds of thousands of computers; two percent of the victims are from Switzerland. The Criminals were able to sign the Software even digital that to draw you as a real Update.
this attack was Discovered – in the meanwhile, the martial name "Shadow Hammer" (twilight's hammer) is wearing – from the security firm Kaspersky. In a blog post he will be described in Detail. Between June and November 2018, the attack took place and was only discovered in January 2019. Kaspersky has subsequently contacted Asus to stop the attack.
According to Kaspersky two percent of the victims of the "shadow hammer" sitting in Switzerland.
Despite the large-scale attack, it had said, the hackers apparently only to a few victims. In the Code of the malicious software, security researchers have found 600 addresses of network adapters. Only if the malicious software has found a suitable address, you will become active in order to load further malware from the net. This is reminiscent of a case two years ago, where the popular Windows-Software CCleaner infected and about the automatic Update feature shipped. Here, too, it came to light that it was only 40 computers in 12 companies (see Also Hacker work from nine to five).
Computer in Chernobyl failed
In another case, the Update of an accounting was infected software, the Trojan "NotPetya". He has taken care of 2017 for a huge damage. Were affected at that time, large and small businesses, and even in the NUCLEAR ruins of Chernobyl, at the time, failed Windows Computer for the measurement of Radiation.
Kaspersky points to another danger, in the be Increase: The so-called supply-chain attacks, i.e. attacks via the supply chain: The Software is introduced at the supplier and passes through the manufacturer in the final products. This can happen on Updates, but also during the fabrication process. The USA have last year established a task force to take countermeasures. The Online magazine "Motherboard" quoted a high-ranking employee of the U.S. foreign intelligence service NSA, says that this new form of Attack came from the category of "Big Deals": As people have planned carefully. Nevertheless, it was the wood, hammer method, if thousands of people were affected, although only a few victims.
Are you affected?
where the attack and who was targeted, Kaspersky found out, or not communicating. Since the malicious software it except it has only a few computers, the vast majority of owners of the Asus PC's and Laptops will be out, even if the Software should be reached via the Update on the device. Kaspersky provides a program that verifies whether the Software is present and whether the device comprises one of the network addresses to which the attack is targeted. Download the. Exe file under kas.pr/shadow hammer. (Editorial Tamedia)
Created: 26.03.2019, 10:38 PM

 After 13 years of mission and seven successive leaders, the UN at an impasse in Libya
After 13 years of mission and seven successive leaders, the UN at an impasse in Libya Germany: search of AfD headquarters in Lower Saxony, amid accusations of embezzlement
Germany: search of AfD headquarters in Lower Saxony, amid accusations of embezzlement Faced with Iran, Israel plays appeasement and continues its shadow war
Faced with Iran, Israel plays appeasement and continues its shadow war Iran-Israel conflict: what we know about the events of the night after the explosions in Isfahan
Iran-Israel conflict: what we know about the events of the night after the explosions in Isfahan Sánchez condemns Iran's attack on Israel and calls for "containment" to avoid an escalation
Sánchez condemns Iran's attack on Israel and calls for "containment" to avoid an escalation China's GDP grows 5.3% in the first quarter, more than expected
China's GDP grows 5.3% in the first quarter, more than expected Alert on the return of whooping cough, a dangerous respiratory infection for babies
Alert on the return of whooping cough, a dangerous respiratory infection for babies Can relaxation, sophrology and meditation help with insomnia?
Can relaxation, sophrology and meditation help with insomnia? Vacation departures and returns: with the first crossovers, heavy traffic is expected this weekend
Vacation departures and returns: with the first crossovers, heavy traffic is expected this weekend “Têtu”, “Ideat”, “The Good Life”… The magazines of the I/O Media group resold to several buyers
“Têtu”, “Ideat”, “The Good Life”… The magazines of the I/O Media group resold to several buyers The A13 motorway closed in both directions for an “indefinite period” between Paris and Normandy
The A13 motorway closed in both directions for an “indefinite period” between Paris and Normandy The commitment to reduce taxes of 2 billion euros for households “will be kept”, assures Gabriel Attal
The commitment to reduce taxes of 2 billion euros for households “will be kept”, assures Gabriel Attal The exclusive Vespa that pays tribute to 140 years of Piaggio
The exclusive Vespa that pays tribute to 140 years of Piaggio Kingdom of the great maxi scooters: few and Kymco wants the crown of the Yamaha TMax
Kingdom of the great maxi scooters: few and Kymco wants the crown of the Yamaha TMax A complaint filed against Kanye West, accused of hitting an individual who had just attacked his wife
A complaint filed against Kanye West, accused of hitting an individual who had just attacked his wife In Béarn, a call for donations to renovate the house of Henri IV's mother
In Béarn, a call for donations to renovate the house of Henri IV's mother Skoda Kodiaq 2024: a 'beast' plug-in hybrid SUV
Skoda Kodiaq 2024: a 'beast' plug-in hybrid SUV Tesla launches a new Model Y with 600 km of autonomy at a "more accessible price"
Tesla launches a new Model Y with 600 km of autonomy at a "more accessible price" The 10 best-selling cars in March 2024 in Spain: sales fall due to Easter
The 10 best-selling cars in March 2024 in Spain: sales fall due to Easter A private jet company buys more than 100 flying cars
A private jet company buys more than 100 flying cars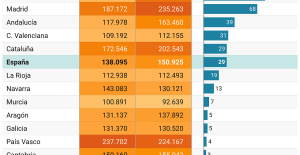 This is how housing prices have changed in Spain in the last decade
This is how housing prices have changed in Spain in the last decade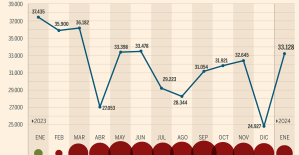 The home mortgage firm drops 10% in January and interest soars to 3.46%
The home mortgage firm drops 10% in January and interest soars to 3.46% The jewel of the Rocío de Nagüeles urbanization: a dream villa in Marbella
The jewel of the Rocío de Nagüeles urbanization: a dream villa in Marbella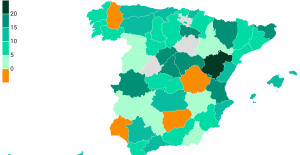 Rental prices grow by 7.3% in February: where does it go up and where does it go down?
Rental prices grow by 7.3% in February: where does it go up and where does it go down? With the promise of a “real burst of authority”, Gabriel Attal provokes the ire of the opposition
With the promise of a “real burst of authority”, Gabriel Attal provokes the ire of the opposition Europeans: the schedule of debates to follow between now and June 9
Europeans: the schedule of debates to follow between now and June 9 Europeans: “In France, there is a left and there is a right,” assures Bellamy
Europeans: “In France, there is a left and there is a right,” assures Bellamy During the night of the economy, the right points out the budgetary flaws of the macronie
During the night of the economy, the right points out the budgetary flaws of the macronie These French cities that will boycott the World Cup in Qatar
These French cities that will boycott the World Cup in Qatar Rally: Neuville and Evans neck and neck after the first day in Croatia
Rally: Neuville and Evans neck and neck after the first day in Croatia Gymnastics: after Rio and Tokyo, Frenchman Samir Aït Saïd qualified for the Paris 2024 Olympics
Gymnastics: after Rio and Tokyo, Frenchman Samir Aït Saïd qualified for the Paris 2024 Olympics Top 14: in the fight for maintenance, Perpignan has the wind at its back
Top 14: in the fight for maintenance, Perpignan has the wind at its back Top 14: Toulon-Toulouse, a necessarily special reunion for Melvyn Jaminet
Top 14: Toulon-Toulouse, a necessarily special reunion for Melvyn Jaminet


















