The number is enormous: 2'692 818'238 lines with access data for Internet services appeared in the network. But millions of E-Mail addresses and passwords in the network unencrypted and so readable.
The IT security researcher Troy Hunt met during his research in a hacker forum on the data leak. It could, at times, to be there, and also on the Cloud service Mega download. The magazine "Wired" called it the biggest Leak, which was previously known to the public.
in terms of the Numbers a little bigger, the two in 2016, known Yahoo-Leaks, one of which, respectively, three billion records were affected would in theory. However, both of these sensitive records are not yet showed up in the publicly viewable part of the network.
22 million passwords published
Otherwise, the "Collection #1", such as the well known data set is named. The origin of the data is exactly, is still unclear. Hunt, according to a variety of Websites are affected. Apparently, the Publishing is concentrated in the collection of a variety of older and newer Leaks.
Hunt wrote in a blog post that it had detected some data, about 140 million E-Mail addresses were also new for him. He have been adjusted for the collection of duplicates-and-dirty records, then approximately 770 million E-Mail are still addresses left, 22 million passwords.
the difference between The two Figures is explained by the fact that many users use different than recommended the same password for more than one page. In addition, different users can happen to use identical passwords, which relates in particular to simple passwords such as "123456".
detours Hacker get account data
With the Leak of the millions of access data are now hackers from all over the world available to the users to spy or to try to get to Shopping and banking data. This happens in the case of such large Leaks often called a "credential stuffing", which translates roughly as "Stuff with logon data". In the process, hackers can fire very long lists with E-Mail-password combinations from automated access to a system of a service, for example on Spotify.
The Software tried independently, with hundreds of thousands of access data sequentially to log in. At this mass, the Chance is not too small to land with some of the combinations of hits and to gain access to user accounts. An analysis of the IT security company Shape Security in the summer of 2018, according to 80 percent of Log-in Attempts to shopping pages from Unauthorized. Almost on a par with the Figures for the web sites of airlines.
user check whether you are affected
"Collection #1"-explorers, Hunt is recognized among professionals as the expert for the security of login data. He has loaded the latest Leak in his database that he has collected since a few years, Leaks. To help Internet users to protect themselves: On its Website haveibeenpwned.com you can check whether you are affected by the current Leak, or older. To do this, you need to enter in the search field, type an E-Mail address for Log-ins.
After a click on the "search" checks the website, whether or not the E-Mail address showed up in one of the Leaks from the past few years. You are not only shows, in which Leak this E-Mail address showed up, however, which password was used – that would be a security problem.
a collection of data "Collection #1", is also not clear which web sites or Apps are affected. Your own data should be affected so, then users should change as soon as possible your passwords for all the services to which this E-Mail address. (Editorial Tamedia)
Created: 17.01.2019, 15:02 PM

 Sydney: Assyrian bishop stabbed, conservative TikToker outspoken on Islam
Sydney: Assyrian bishop stabbed, conservative TikToker outspoken on Islam Torrential rains in Dubai: “The event is so intense that we cannot find analogues in our databases”
Torrential rains in Dubai: “The event is so intense that we cannot find analogues in our databases” Rishi Sunak wants a tobacco-free UK
Rishi Sunak wants a tobacco-free UK In Africa, the number of millionaires will boom over the next ten years
In Africa, the number of millionaires will boom over the next ten years WHO concerned about spread of H5N1 avian flu to new species, including humans
WHO concerned about spread of H5N1 avian flu to new species, including humans New generation mosquito nets prove much more effective against malaria
New generation mosquito nets prove much more effective against malaria Covid-19: everything you need to know about the new vaccination campaign which is starting
Covid-19: everything you need to know about the new vaccination campaign which is starting The best laptops of the moment boast artificial intelligence
The best laptops of the moment boast artificial intelligence Bitcoin halving: what will the planned reduction in emissions from the queen of cryptos change?
Bitcoin halving: what will the planned reduction in emissions from the queen of cryptos change? The Flink home shopping delivery platform will be liquidated in France
The Flink home shopping delivery platform will be liquidated in France Bercy threatens to veto the sale of Biogaran (Servier) to an Indian industrialist
Bercy threatens to veto the sale of Biogaran (Servier) to an Indian industrialist Switch or signaling breakdown, operating incident or catenaries... Do you speak the language of RATP and SNCF?
Switch or signaling breakdown, operating incident or catenaries... Do you speak the language of RATP and SNCF? The main facade of the old Copenhagen Stock Exchange collapsed, two days after the fire started
The main facade of the old Copenhagen Stock Exchange collapsed, two days after the fire started Alain Delon decorated by Ukraine for his support in the conflict against Russia
Alain Delon decorated by Ukraine for his support in the conflict against Russia Who’s Who launches the first edition of its literary prize
Who’s Who launches the first edition of its literary prize Sylvain Amic appointed to the Musée d’Orsay to replace Christophe Leribault
Sylvain Amic appointed to the Musée d’Orsay to replace Christophe Leribault Skoda Kodiaq 2024: a 'beast' plug-in hybrid SUV
Skoda Kodiaq 2024: a 'beast' plug-in hybrid SUV Tesla launches a new Model Y with 600 km of autonomy at a "more accessible price"
Tesla launches a new Model Y with 600 km of autonomy at a "more accessible price" The 10 best-selling cars in March 2024 in Spain: sales fall due to Easter
The 10 best-selling cars in March 2024 in Spain: sales fall due to Easter A private jet company buys more than 100 flying cars
A private jet company buys more than 100 flying cars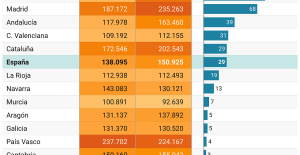 This is how housing prices have changed in Spain in the last decade
This is how housing prices have changed in Spain in the last decade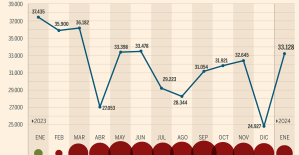 The home mortgage firm drops 10% in January and interest soars to 3.46%
The home mortgage firm drops 10% in January and interest soars to 3.46% The jewel of the Rocío de Nagüeles urbanization: a dream villa in Marbella
The jewel of the Rocío de Nagüeles urbanization: a dream villa in Marbella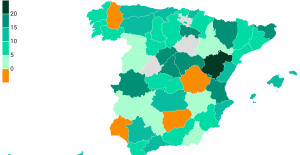 Rental prices grow by 7.3% in February: where does it go up and where does it go down?
Rental prices grow by 7.3% in February: where does it go up and where does it go down? With the promise of a “real burst of authority”, Gabriel Attal provokes the ire of the opposition
With the promise of a “real burst of authority”, Gabriel Attal provokes the ire of the opposition Europeans: the schedule of debates to follow between now and June 9
Europeans: the schedule of debates to follow between now and June 9 Europeans: “In France, there is a left and there is a right,” assures Bellamy
Europeans: “In France, there is a left and there is a right,” assures Bellamy During the night of the economy, the right points out the budgetary flaws of the macronie
During the night of the economy, the right points out the budgetary flaws of the macronie These French cities that will boycott the World Cup in Qatar
These French cities that will boycott the World Cup in Qatar Europa Conference League: the semi-final flies to Lille, which loses to the wire against Aston Villa
Europa Conference League: the semi-final flies to Lille, which loses to the wire against Aston Villa Lille-Aston Villa: Cash disgusts Lille, the arbitration too... The tops and the flops
Lille-Aston Villa: Cash disgusts Lille, the arbitration too... The tops and the flops Handball: Les Bleues in the same group as Spain at Euro 2024
Handball: Les Bleues in the same group as Spain at Euro 2024 Europa Conference League: for Létang, Martinez “does not have the attitude of a high-level athlete”
Europa Conference League: for Létang, Martinez “does not have the attitude of a high-level athlete”


















